Why This Experiment Exists
Lately, I have been revisiting an idea that has been on my mind for many years:
how to gradually move away from US-centric software products.
By now, this has turned into a personal experiment —
part technical challenge, part entertainment, part philosophical exercise.
The goal is not ideological purity, but conscious trade-offs.
My core premise has remained unchanged over the years:
minimize unnecessary data exposure.
Given the current political climate — especially developments in US politics —
the topic of digital sovereignty feels more relevant than ever.
Digital sovereignty means retaining control over software dependencies,
data flows, and infrastructure — even if that comes at the cost of convenience.
The Messaging Problem: Technology vs. People
Several years ago, I managed to stay away from
WhatsApp for a surprisingly long time.
From a purely technical perspective, this was trivial.
Alternatives like
Signal
are feature-complete, cryptographically solid, and often superior by design.
The real obstacle was not software — it was
human network effects.
- Most non-technical users do not care about metadata collection
- Surveillance capitalism is abstract and invisible
- Installing “yet another app” is perceived as friction
As a result, WhatsApp remains the lowest common denominator for social
communication.
Quitting WhatsApp is not a technical decision — it is a social one.
At this point, I am not willing to accept the social cost of full abstinence.
Too many people would become reachable only via
SMS, phone calls, or email.
GrapheneOS: A Different Baseline
Instead of removing WhatsApp entirely, I decided to rethink the
operating system layer.
I installed
GrapheneOS
on my daily driver — a Pixel 9.
The installation process itself is refreshingly modern:
a browser-based installer, excellent documentation, and a total setup time
of roughly 20 minutes.
While GrapheneOS is still Android under the hood, it deliberately ships
without Google Play Services and without requiring
a Google account.
Google services are optional, sandboxed, and installed per user profile —
not globally.
There is, of course, a certain irony in the fact that GrapheneOS officially
supports only Google Pixel devices — hardware built by Google itself.
Compartmentalization with Shelter
To further isolate untrusted applications, I installed
Shelter.
Shelter is essentially a user-friendly frontend for Android’s
work profile feature.
It allows apps to run in a logically separate environment with strict
boundaries.
I created a dedicated Work Profile and moved WhatsApp into it.
This turns WhatsApp into a semi-contained subsystem.
What This Enables
- Completely separate contacts database
- No implicit access to my main address book
- GPS access denied
- Photo library access denied
For now, location and media access are fully blocked.
The experiment is to see how far usability can be stretched without
completely breaking the user experience.
Important Clarification
This is not about hating WhatsApp.
Quite the opposite.
I genuinely enjoy WhatsApp, especially the
Status feature and its low-friction sharing model.
The issue is not social sharing —
it is the opaque backend machinery.
US-based cloud infrastructures, unclear data flows, and the lack of
transparency around content processing are what I am increasingly
unwilling to accept blindly —
especially when it comes to photos of my children.
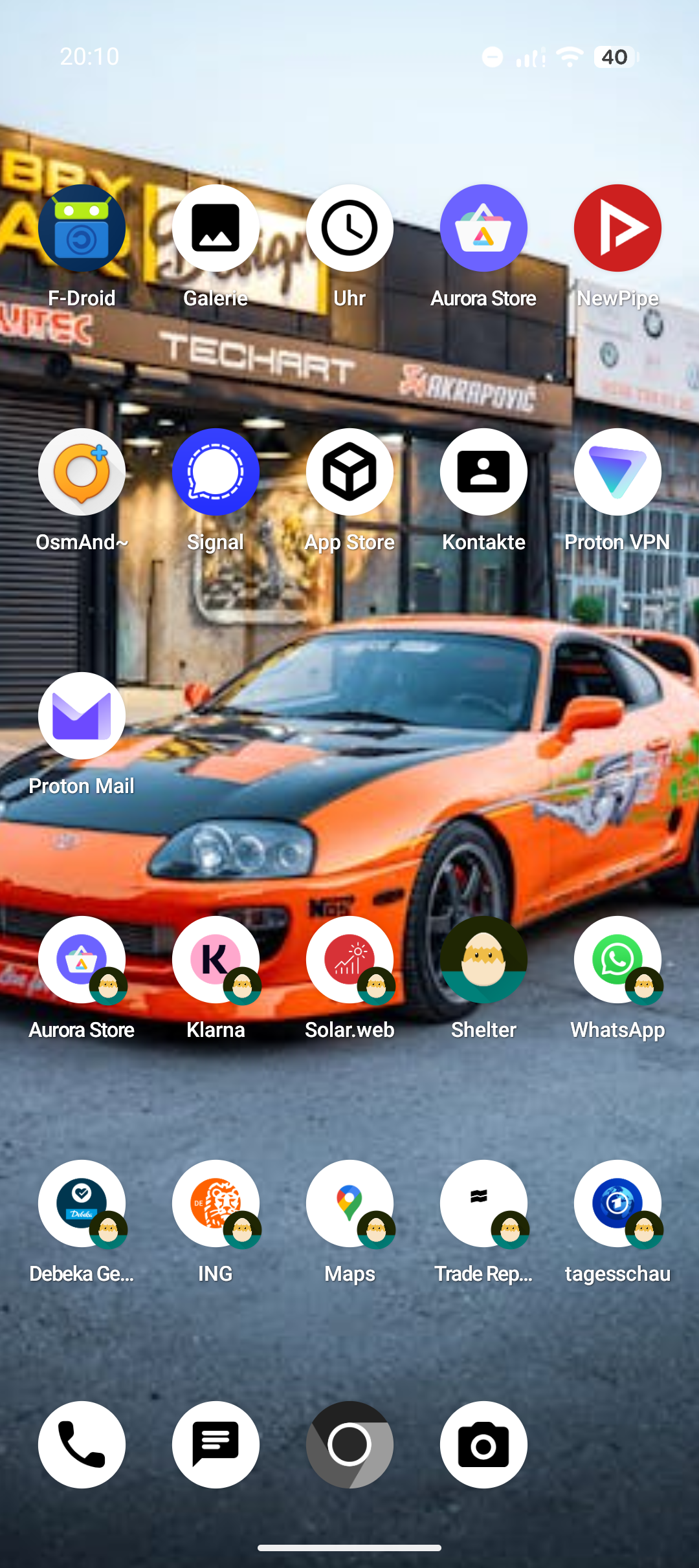
Visual Trust Boundaries: Reading the App Drawer
The screenshot above illustrates how this compartmentalization manifests itself
in everyday usage.
The app drawer is effectively split into two distinct trust zones.
In the upper section, you can see applications that I consider
trusted and therefore run in my primary user profile without additional
restrictions.
These apps have either been audited to a reasonable extent, are open source, or
are sufficiently constrained in their data access patterns.
The lower section contains applications that have been
deliberately crippled via
Shelter.
These apps run exclusively inside the Work Profile and are treated as
inherently untrusted.
Apps managed by Shelter are easy to identify.
They are marked with a small icon depicting a
blindfolded head — a subtle but constant reminder that these applications
are sandboxed, permission-constrained, and isolated by design.
This visual separation is not just cosmetic.
It serves as a cognitive security cue:
a quick reminder of which apps operate within my trust boundary and which ones
are confined to a tightly controlled execution environment.
Over time, this has proven surprisingly useful.
It reinforces a mental model where applications are no longer equal peers on the
system, but explicitly categorized based on
trust level,
data access,
and potential blast radius.
What Comes Next
This setup is still evolving.
I will continue testing, adjusting permissions, and observing real-world
limitations.
Expect follow-up posts on:
- Push notifications and Google services in sandboxed profiles
- Battery behavior of work profiles
- Long-term usability trade-offs
More updates will follow.